The annual Las Vegas Blackhat security conference draws great attention from the media as the showpiece for trendy cyber security topics. From its inception in 1997, Blackhat has grown into a global conference series with additional stops in Abu Dhabi, Barcelona, and Washington DC. The conference includes the latest researchers from leading security companies such as Mandiant and McAfee. It also features the latest computer hacks and exploits for everything from commercial point of sale devices to mobile phones and broadband Internet modems.
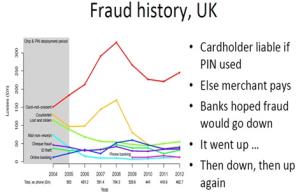
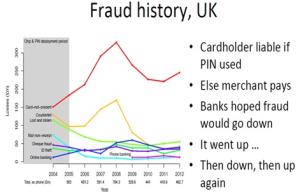
University of Cambridge study showing overall credit card fraud did not drop after introduction of chip and pin security technology by MasterCard and Visa
While attending Blackhat this year, I discussed the latest credit card system exploits from security experts from the University of Cambridge, learned how the most dangerous viruses are designed to avoid detection from researchers at Intel Brazil, and discussed advancements in security risk management practices with employees of the Department of Homeland Security and the FBI.
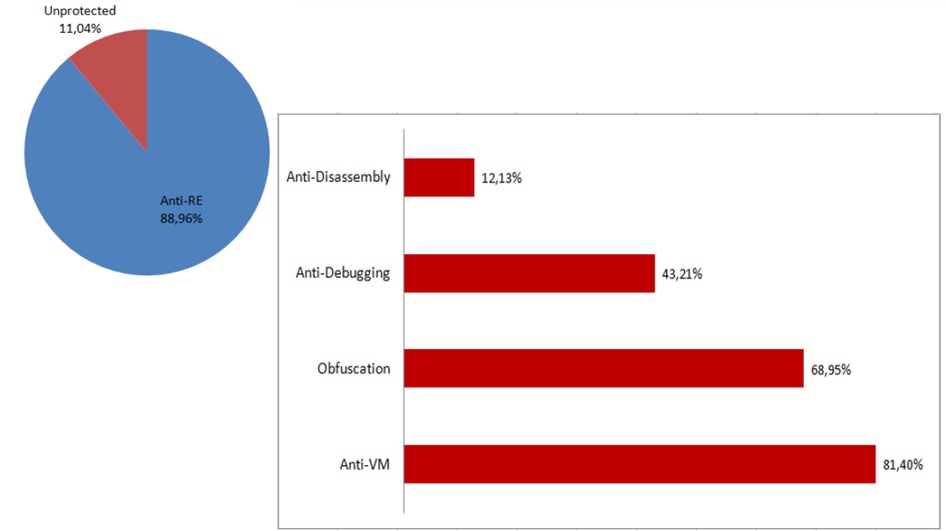
Research from Intel Brazil showing techniques hackers use 89% of the time to avoid detection by malware scanners
In addition to attending a diverse menu of security briefings, I participated in a two day boot camp covering new techniques in identifying and responding to network security threats. The security team at Mandiant has put together a free, open source collection of security tools available at no charge that rivals the best commercial incident response products on the market. The techniques and tools presented at Blackhat is truly state of the art and goes to show what a growing community of dedicated security professionals is capable of in responding to the current cyber security threat.
While the training was truly phenomenal, it was also quite terrifying. The hacker demonstrations at the conference showed that our information is not safe on the Internet. A great deal of work has to be done to combat the increasingly complex attacks against our information infrastructures. Attackers are out in front of the defenders in both sophistication of techniques employed and the ability adroitly apply a catalogue of various techniques in customized attacks that thwart the best of our digital defenses. This is a global information war that the West is quickly losing.
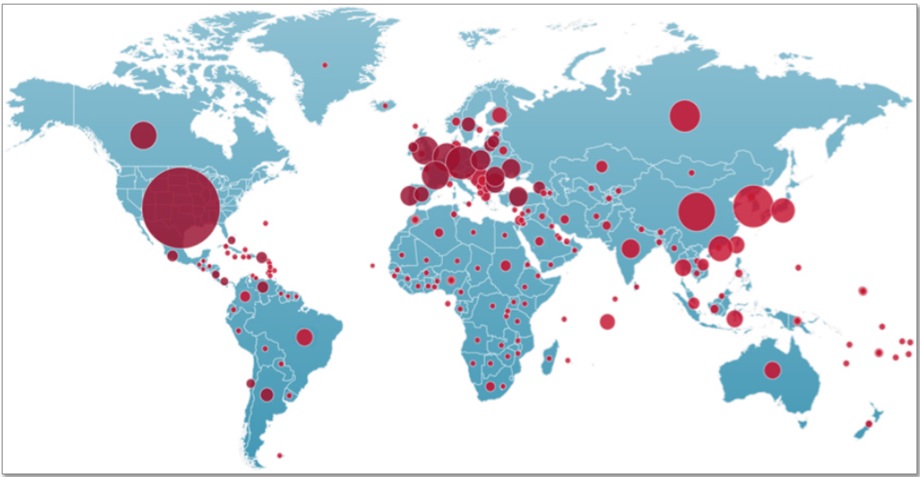
Briefing ‘Leviathan' showing over 30 million instances of command and control botnet activity across the planet during 2013
According to former Defense Secretary Robert Gates, the Pentagon is “desperately short of people who have capabilities (defensive and offensive cyber-security war skills) in all the services and we have to address it.”